Is FIDO2 Ready for the Quantum Era?

“an oil painting of a scientist logging into a website” by DALL-E.
Weak passwords are a major security vulnerability in today’s Internet. To tackle this issue, the Fast IDentity Online (FIDO) Alliance set out to define a secure protocol for passwordless identity authentication using ‘security devices’, such as smartphones or dedicated USB or NFC hardware tokens. With over forty key companies, including Amazon, Apple, Google, Intel, Microsoft, RSA, VISA, and Yubico, the FIDO Alliance has improved secure log in for the wider public, enterprise employees, and government members. This post will explain recent research results about whether the de facto standard for passwordless authentication, called the FIDO2 protocol, is ‘quantum-ready’.
This blog post is a short introductory version of the paper “FIDO2, CTAP 2.1, and WebAuthn 2: Provable Security and Post-Quantum Instantiation” by Nina Bindel, Cas Cremers, and Mang Zhao which has been accepted at the 44th IEEE Symposium on Security and Privacy (May 22-25, 2023, San Francisco, CA, US). It can be accessed on IACR eprint 2022/1029.
The FIDO2 protocol is run between web applications (also called ‘relying parties’, such as the Google or Apple services you might log in to), web browsers (also called ‘clients’), authenticator hardware tokens (such as a smart phone or the above-mentioned USB tokens), and users. It is defined using two subprotocols: WebAuthn and CTAP (Client To Authenticator Protocol).
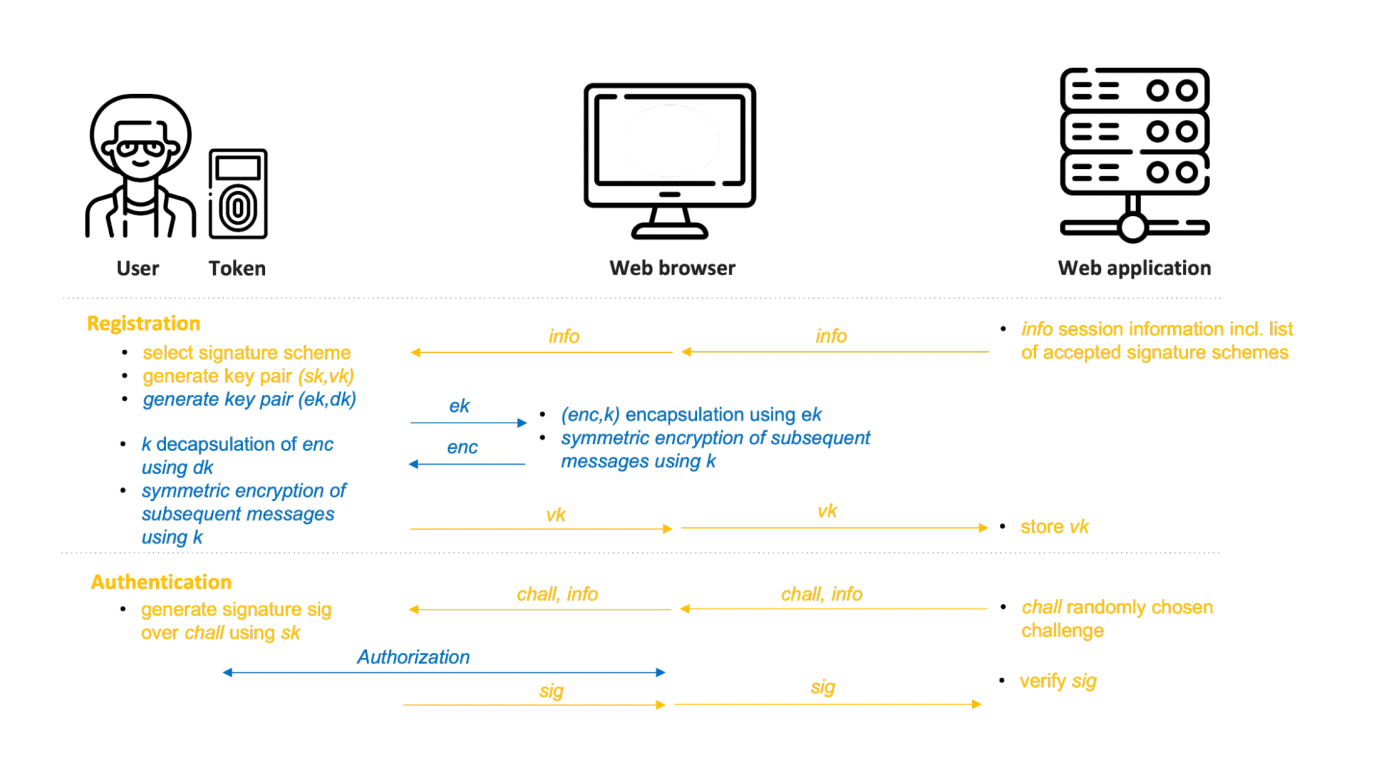
Simplified FIDO2 protocol consisting of WebAuthn (orange) and CTAP (blue).
As depicted in the figure, WebAuthn is run between a web application, a web browser, and an authenticator hardware token. The first step in the WebAuthn protocol is for the user to register their authenticator hardware token with a web application. During this registration, a key pair consisting of a secret signing key and a public verification key is generated on the token. While the secret signing key remains on the token, the public verification key is communicated to the web application via the web browser. During ‘authentication’ (i.e., every time the user wants to log into the web application), the web application sends a random string (a ‘challenge’) to the token. The token then signs this random challenge digitally using the respective secret signing key. After receiving the signature via the web browser, the web application can verify the correctness of the signature using the public verification key and therefore be sure that the token used for authentication is the one that has been registered by the user. If the signature is correct, the user is automatically logged in, without using any password.
In contrast to WebAuthn, CTAP is only run between an authenticator hardware token and a web browser using the user’s input such as pressing a button on the token or entering a PIN. The purpose of CTAP is to restrict which web browser is allowed to use the token’s API (Application Programming Interface). During CTAP, using the user’s input, the token and web browser agree on a shared secret that is then used to (symmetrically) encrypt the subsequent communication between the web browser and token. Together, WebAuthn and CTAP ensure that an authenticator token initially registered in the web application is needed to log in, which reduces the chances of user impersonation due to brute-force attacks on passwords, social-engineering attacks or leaked password databases.
The FIDO2 protocol supports many different modes and options, leaving them to the web applications or the token manufacturer’s choice. For example, the specifications allow for
- different attestation modes to guarantee certain properties (e.g., a level of security certification) of the token to the web application,
- different ways of how the user is involved (e.g., whether it suffices that the user presses a single button or whether they have to enter a PIN code),
- different modes to store the secret keys of the potentially very space-constrained hardware tokens,
- different signature schemes that the web application accepts and the token supports.
The full research paper associated with this blog post (based on a first model by Barbosa, Boldyreva, Chen, and Warinschi) models the WebAuthn, CTAP, and their combination in FIDO2 and defines what it means for these protocols to be ‘secure’. This is an important approach to ‘prove’ that these satisfy desired security goals under certain conditions (ideally as close to reality as possible) and, therefore, to exclude or detect attacks against them. In addition, the full paper also analyzes whether the FIDO2 protocol is ‘quantum-ready’, i.e. whether the security guarantees also hold against quantum adversaries assuming quantum-resistant (also called ‘post-quantum’) cryptographic algorithms are used.
Let’s take a closer look at what that means. The FIDO2 protocol allows the use of the following cryptographic algorithms: the signature schemes RSA and ECDSA during WebAuthn, and a combination of the key exchange ECDH with the symmetric encryption AES during CTAP. While all of these cryptographic algorithms are believed to be secure now, large fault-tolerant quantum computers will be able to break the public-key algorithms therein (i.e., RSA, ECDSA, and ECDH will not be secure anymore). That means alternative algorithms that are secure, even in the presence of large quantum computers, need to be used (visit our blog post for more information about the quantum threat and actions to maintain security in the quantum era). While there are replacements for the signature schemes, there is no direct replacement for the key exchange protocol ECDH. Instead, a different cryptographic primitive, namely, a key encapsulation mechanism (KEM), has to be used. As it turns out and has been proven in the full paper, the latest FIDO2 protocol accounted for that and is offering an option to use KEMs as a way to agree on a key during CTAP.
A next step is to use combinations of traditional and quantum-resistant algorithms (so-called ‘hybrid’ algorithms) to ensure security, even if one of them is broken. Several standardization agencies, such as NIST, recommend this approach for the near-term. The need to deploy post-quantum algorithms is urgent, but many of the post-quantum algorithms are still rather new and need more cryptanalysis to be sure that they are secure enough to be used in a standalone manner (visit our blog post for more information about recent attacks against some post-quantum algorithms). As the full paper points out, the current FIDO2 specifications can be extended to allow hybrid KEMs and hybrid signature schemes in a specification-compliant way. For example, during the registration of WebAuthn, the web application sends a list of algorithms that it accepts. The token then uses the first entry in this list that it supports to sign the web application’s challenge during authentication. Depending on the web application’s choice, this list could include only traditional algorithms (variant (a) of the figure below), it could include only a hybrid scheme to only accept post-quantum secure solutions (variant (b) of the figure), or it could include both hybrid and traditional algorithms (variant (c) of the figure). The latter’s advantage is that it offers post-quantum secure options to new tokens that can already support post-quantum algorithms and is backwards-compatible with older tokens that only support traditional cryptography.
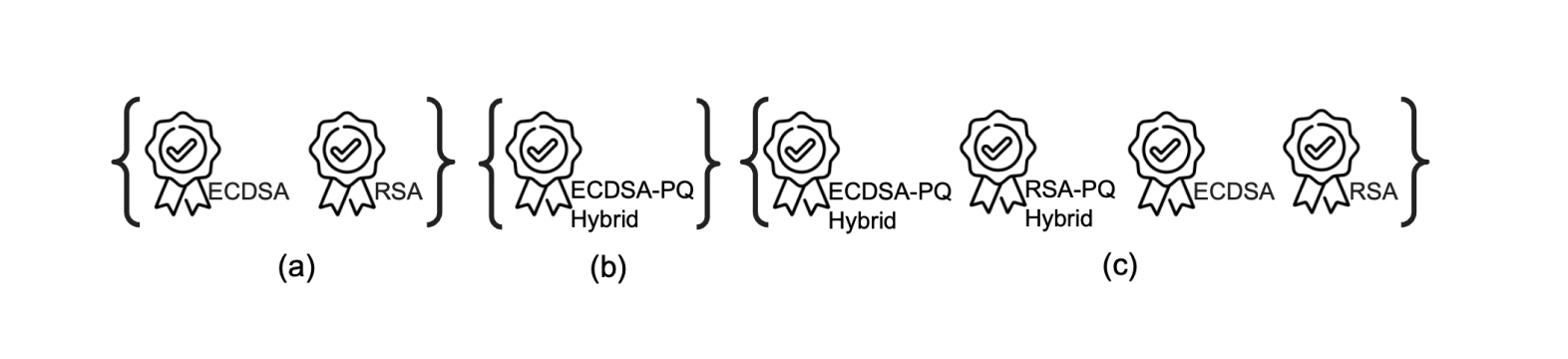
(Future) Instantiations for the web applications’ list of supported signature schemes; a) current list with choices between ECDSA and RSA, b) quantum-resistant combination of traditional and post-quantum hybrid signatures as the only option, c) hybrid signature in addition to traditional schemes to offer quantum-resistance while being backwards-compatible.
While the results in the full paper take an important step forward regarding the formal analysis of FIDO2’s (post-quantum) security, many more steps should be taken. For example, the paper analyzes specific modes of FIDO2, such as a mode that does not use any attestation. Moreover, based on the theoretical analysis, post-quantum algorithms that are best suited for the different FIDO2 modes need to be selected and implemented on the very constrained hardware tokens.
The migration to post-quantum secure cryptography is a long road of opportunities and challenges. For FIDO2, it has been the perfect opportunity to revisit the protocol and to set the tracks to enable a post-quantum migration.
