When Crypto-agility Meets Cybersecurity: Challenges and Opportunities

“An oil painting of a hacker trying to steal data from a company” by DALL-E.
Cryptography is an essential element in the protection of data and communications in any modern company. What type of cryptography to use and how easy it is to adapt it to new algorithmic developments, new architectures or new products necessities is a challenge that must be tackled relentlessly. We summarize this concern and opportunity with the term crypto-agility.
A typical introduction to crypto-agility can be obtained from Wikipedia:
Cryptographic agility (also referred to as crypto-agility) is a practice paradigm in designing information security protocols and standards in a way so that they can support multiple cryptographic primitives and algorithms at the same time. Then the systems implementing a particular standard can choose which combination of primitives they want to use. The primary goal of cryptographic agility was to enable rapid adaptations of new cryptographic primitives and algorithms without making disruptive changes to the systems’ infrastructure.
Cryptographic agility acts as a safety measure or an incident response mechanism when a cryptographic primitive of a system is discovered to be vulnerable. A security system is considered crypto agile if its cryptographic algorithms or parameters can be replaced with ease and is at least partly automated. The impending arrival of a quantum computer that can break existing asymmetric cryptography is raising awareness of the importance of cryptographic agility…
However, the concept of crypto-agility goes a step further and complements the best cybersecurity practices and standards in different ways. Lately, it has become a pivotal paradigm and is referred to in an ever-increasing list of resources, including the last US NSM (National Security Memorandum). In 2022, the U.S. White House issued National Security Memorandum 10, affirming agile cryptography and mandating that federal agencies comply with quantum-resistant encryption algorithms approved by the National Institute for Standards and Technology (NIST). The memorandum applies to critical infrastructure “so vital to the United States that their incapacitation or destruction would have a debilitating effect on the Nation’s security, economy, public health and safety, or any combination thereof”.
“Central to this migration effort will be an emphasis on cryptographic agility, both to reduce the time required to transition and to allow for seamless updates for future cryptographic standards. This effort is an imperative across all sectors of the United States economy, from government to critical infrastructure, commercial services to cloud providers, and everywhere else that vulnerable public-key cryptography is used.” NSM 10
In this post, we would like to discuss the challenges and opportunities that crypto-agility must address in its incorporation into real environments with well-defined cybersecurity frameworks and philosophies. Specifically, we focus on the NIST cybersecurity framework, the MITRE ATT&CK framework, and zero-trust security models.
In the day-to-day running of an organization, cybersecurity concerns are multiple and continuously growing. They must be addressed, in many cases, with limited budgets and resources. It is in this scenario that cyber security frameworks, and best practices, allow us to gradually solve problems and to measure, when possible, the short, medium and long-term return on investment in the countermeasures deployed. The whole company, and especially the chief information security officer (CISO), are undoubtedly involved.
Crypto-agility brings real and actionable value to an organization’s cybersecurity. Let’s analyze it on a case-by-case basis in the security frameworks and common recommendations in companies.
Crypto-agility meets the NIST Cybersecurity framework
The National Institute of Standards and Technology (NIST) Cybersecurity framework is a set of guidelines for mitigating organizational cybersecurity risks based on existing standards, guidelines, and best practices. The framework “provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage those outcomes”, becoming a de facto cybersecurity standard for much of the cybersecurity industry.
This framework is composed of three components: the Framework Core, the Framework Implementation Tiers (“provide context on how an organization views cybersecurity risk and the processes in place to manage that risk…”), and the Framework Profiles (“represents the outcomes based on business needs…”). Each Framework component reinforces the connection between business/mission drivers and cybersecurity activities.
Although cryptography and crypto agility can impact the entire framework, the Framework Core is one of the most important parts to focus on:
“The Framework Core is a set of cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors. The Core presents industry standards, guidelines, and practices in a manner that allows for communication of cybersecurity activities and outcomes across the organization from the executive level to the implementation/operations level. The Framework Core consists of five concurrent and continuous Functions—Identify, Protect, Detect, Respond, Recover. When considered together, these Functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk…”
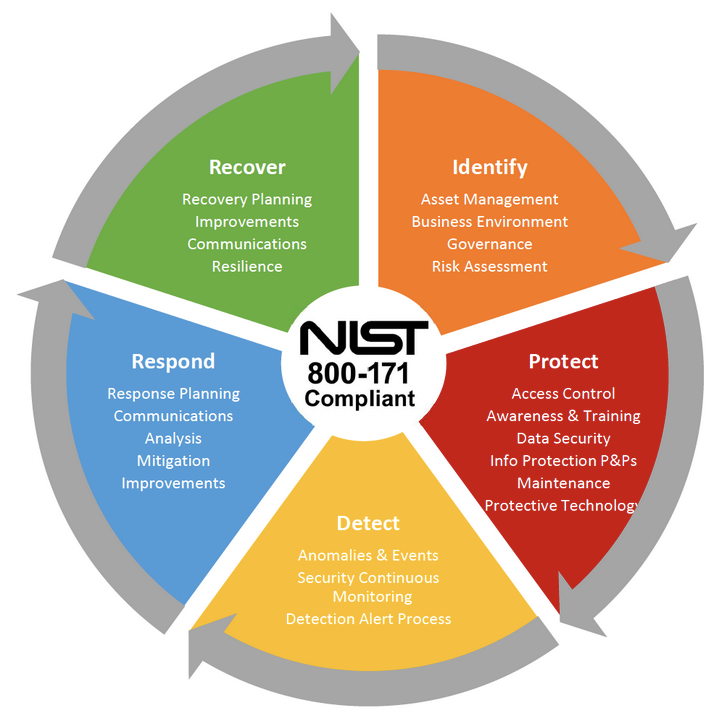
Illustration 1. Cybersecurity lifecycle covered by NIST 800-171 framework - https://www.nist.gov/cyberframework
Looking at the parts into which this framework is divided, we can quickly observe not only how crypto-agility perfectly complements this framework, but also how its use can allow for better performance of the specific categories that need to be covered.
First, in the Identify category, observability components can identify devices, users or processes that use a certain type of cryptographic algorithms or protocols. This characterization provides additional information for efficient risk management and the design of agile cryptographic policies and procedures suitable for regulatory compliance and governance.
Second, in the Protect category, crypto-agility becomes of paramount importance. Having the ability to identify where, when, how and by whom cryptography is used is vital for data protection. This feature is especially key when considering the need to modify cryptography for new secure approaches, such as post-quantum cryptography. This category benefits from cryptographic agility as it enables the utilization of more adequate and forward-looking cryptographic algorithms and protocols.
Cryptographic failures are the second most common weakness - OWASP Top 10- https://owasp.org/www-project-top-ten -. Many attacks come from an incorrect and disorderly use of cryptography. Being able to detect cryptographic misuse or data breaches allows you to make quick, informed and legally compliant decisions.
Finally, the Detect category covers one of the classic cybersecurity foundations. Detecting anomalies and enabling continuous security monitoring is a complex topic that requires a significant investment of resources and skilled professionals. Crypto agility allows us to complement this detection by focusing on the misuse of cryptography. This concept can be better understood by analyzing the attackers’ model as can be done with the MITRE ATT&CK framework in the next section.
The categories Respond and Recover may seem far removed from cryptography. However, when cryptography is breached or needs to be adapted to better respond to an incident, their management becomes critical.
Crypto-agility meets the MITRE ATT&CK framework
The best way to optimize the cybersecurity budget when it comes to reducing cyber-attacks is to know the tactics, techniques and procedures of the attackers (TTPs). In classical cybersecurity literature, this is described by the kill-chain concept introduced by Lockheed Martin. The kill-chain defines the set of actions required by a cyber attacker to achieve its goal. If an organization can avoid one or more of them, it could interrupt the kill-chain and stop the attack. It is at this point where the MITRE ATT&CK framework is so useful for organizations.
MITRE ATT&CK is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
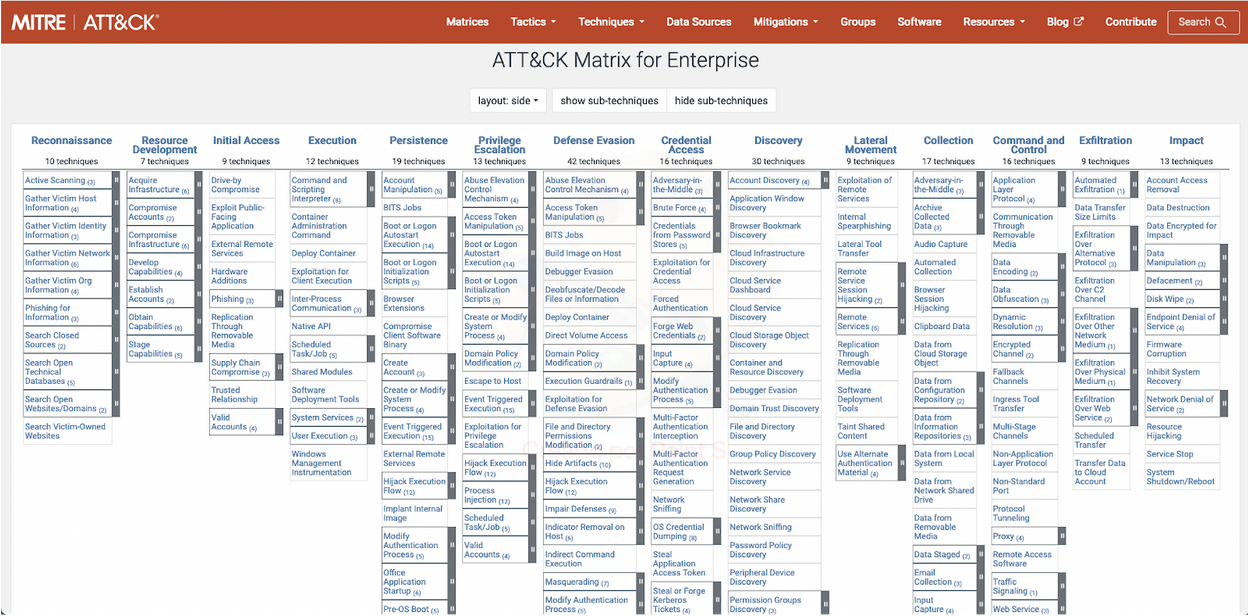
Illustration 2. This map represents (kill-chain) combinations of techniques and sub-techniques that an attacker could use to compromise an organization. MITRE ATT&CK framework studies and details them, facilitating the creation of countermeasures - https://attack.mitre.org/matrices/enterprise/
What is interesting about crypto-agility when the MITRE ATT&CK framework is applied? The quick answer is that it uses cryptographic inventory and monitoring technologies to identify misconfigurations and weaknesses which can be exploited by attackers. Additionally, detection of cryptography used where not expected can be considered an indicator of compromise. Finally, being able to seamlessly choose which algorithms or protocols to use according to some observed events becomes a crucial functionality.
Monitoring the use of cryptography in the organization’s networks, devices, and users provides a huge amount of information to help stop many of the phases used by cyber attackers today. Typical stages where cryptography might be useful from the attacker’s point of view are: Reconnaissance, Initial access, Discovery, Lateral Movement, Credential access, Command & Control and Exfiltration phases. Specific examples can include unexpected cipher combinations in TLS requests (Reconnaissance), high entropy in otherwise batch communications (Command & Control) or high CPU loads due to symmetric encryption (preparation for Exfiltration).
Knowing what cryptography is used, who uses it, when it is used and where it is used could allow us to detect encrypted communications, obfuscated files, attempts to evade security measures, ransomware, information exfiltration, and fingerprinting of malicious servers. All this information can be automated and connected to the detection infrastructure and threat-hunting technologies.
Crypto-agility prepares companies to adapt in the medium term to modern cryptographic management practices (new algorithms, architectures or challenges). In the short term, it adds an incredible amount of value from a cybersecurity point of view to model potential attackers and be able to plan what responses to stop them.
Crypto-agility meets zero-trust philosophy
On May 12, 2021, US President Joe Biden signed an Executive Order on Improving the Nation’s Cybersecurity. The executive order repeatedly emphasized on modernizing the current approach to cybersecurity by advancing towards zero-trust architecture.
The zero-trust security model describes a cybersecurity paradigm where every device and user should not be trusted by default. In 2018, NIST and NCCoE published SP 800-207, zero-trust Architecture as a collection of concepts and ideas designed to reduce the uncertainty in enforcing accurate, per-request access decisions in information systems and services in the face of a network viewed as compromised. A zero-trust architecture (ZTA) is an enterprise’s cyber security plan that utilizes zero-trust concepts and encompasses component relationships, workflow planning, and access policies.
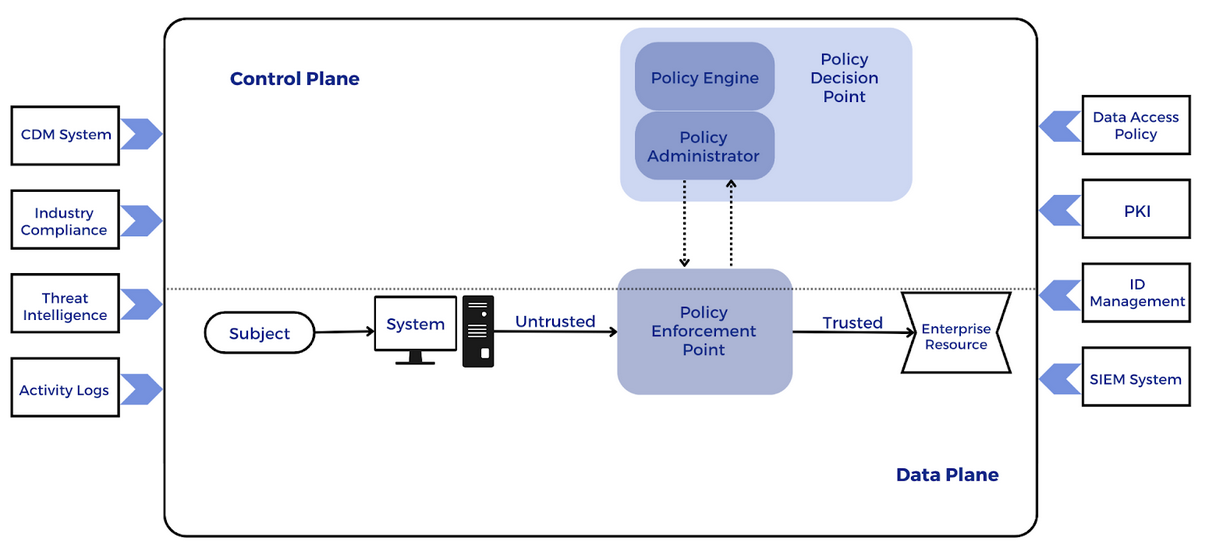
Illustration 3. Image based on Core zero-trust Logical Components from NIST SP 800-207
The above can be summarized as follows:
- From a cybersecurity point of view, our architectures and systems must follow a zero-trust philosophy. Perimeter security (e.g., having an internal network where devices are trusted behind a barrier) is not enough today.
- All users, devices and ’transactions’ must be scrutinized through policy-based access controls (identity management) and strong authentication/authorisation mechanisms. To achieve this, identity and behavioral security governance is essential.
- The simpler it is, the easier it is to measure. The use of micro-segmentation and software-defined countermeasures (“perimeters”) will allow you to make better decisions by adapting to user behavior.
- Enables in-depth analysis to strengthen incident detection and response. Global visibility into users, devices, data, networks and workflows.
Crypto-agility plays an important role in two central elements of this philosophy:
1. Cryptography is the basis of zero-trust Principles
The first crucial (practical) component of zero-trust security is explicit verification. Identity management, which includes first authentication mechanisms and then authorization procedures, requires robust cryptographic protocols, architectures and algorithms. Cryptographic validation is ubiquitously present in confidentiality, integrity, authenticity, availability or non-repudiation. Digital signatures, traditional multi-factor authentication (MFA) such as OTPs (One-time passwords) and biometric authentication are examples of this concept. In addition, crypto-agility is a fundamental pillar in the protection of endpoints, apps, infrastructure, network traffic (TLS, S/MIME, encrypted DNS,…), etc. A true zero-trust architecture is inconceivable without the ability to reliably control the cryptography in use and the flexibility in architectures, software or hardware to adapt or modify the underlying cryptography with new approaches, for example, those based on post-quantum cryptography.
The second one is to assume the breach. In a real scenario, where the attacker is inside our organization, networks or endpoints, the protection of information is vital. Data protection regulations such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA) make it mandatory to take appropriate security measures to protect customers’ personally identifiable information (PII). This implies that all sensitive data must be stored, protected and encrypted.
Data in transit (via TLS or any other cryptographic protocol), data at rest (database, applications, endpoints, etc.) and data in use, especially in RAM or used to perform calculations on the endpoint (“trusted execution environment” and “confidential computing”) must be considered carefully.
The need to know what cryptography is being used, where, by whom and how to improve capabilities to minimize SNDL attacks (Store Now Decrypt Later). When encrypted information is stolen or intercepted, crypto-agility offers the potential for increased security of zero-trust architectures.
2. Paradigms of policy-based access controls
In essence, crypto-agility consists of having the ability to define and use cryptographic policies that allow cryptosystems to be adapted to specific usage scenarios or based on the expected attacker model and security guarantees. The most sensible approach is to use an access control architecture based on the XACML (Extensible Access Control Markup Language) philosophy. This approach enables an attribute-based access control policy language or XML-based language, designed to express security policies and access requests to information.
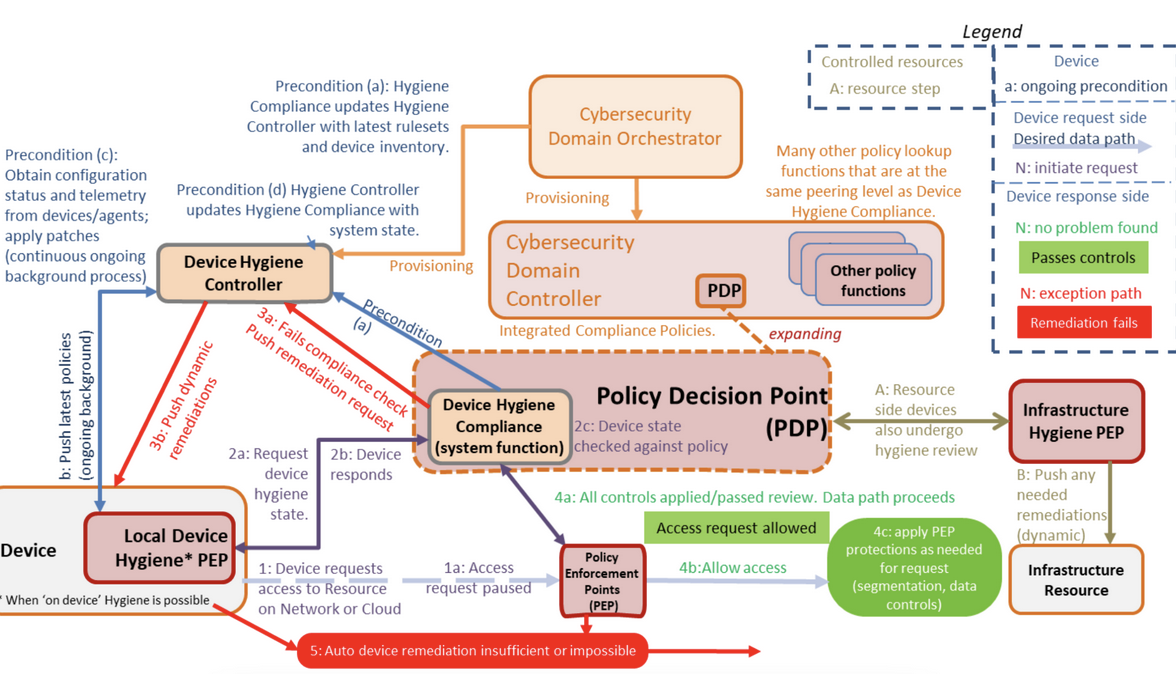
Illustration 4. Example of XACML architecture to manage “device hygiene” based on DoD zero-trust Reference Architecture (Nov 2022)
zero-trust architectures are precisely based on these principles, which makes it conceptually attractive to use the same architecture to add the extra advantages that crypto-agility incorporates in an organization.
Why Crypto-Agility is critical for your organization
Understanding the positive impact that crypto-agility has on corporate cybersecurity and current frameworks, we can summarize our findings:
0. Cryptographic agility is the ability to encapsulate cryptographic primitives or algorithms, making it easy to switch and replace these primitives as new standards emerge. An agile cryptographic security system can inventorize cryptography and, if needed, adapt it to evolving compliance requirements and threats, without requiring significant infrastructure changes and ensuring business continuity.
1. Know your organization in terms of cryptographic usage and enable capabilities to continuously monitor the environment.
2. Agility does not mean “speed”. It means using the right security technology at the right time for the right person/department/organization.
Crypto-agility should allow new algorithms and protocols to be deployed to specific scenarios once they have been validated so that their modification does not negatively impact the communications architecture, overall security or the application of current regulations.
3. Investing in crypto-agility positions companies strategically in the medium and long term and helps solve cybersecurity problems in the short term.
4. Crypto-agility provides technological sovereignty and cost reduction.
The identification of cryptographic technologies allows the detection of unused functionality and duplicate technologies, which is common in organizations and enables the redesign of processes and architectures and cost savings.
Mitigating cryptographic risks and evolving to post-quantum technologies is a priority to ensure digital sovereignty. The importance of this topic can be seen in a memorandum issued in November 2022 by the White House to instruct agencies to comply with National Security Memorandum 10 (NSM-10) on promoting U.S. leadership in quantum computing while mitigating the risk of vulnerable cryptographic systems (May 4, 2022). It highlights the need to designate a cryptographic inventory and a prioritized inventory of information systems and assets that contain quantum-vulnerable cryptographic systems, as well as an assessment of the funding required to migrate the inventoried information systems and assets to post-quantum cryptography.
All of these principles provide insight into why crypto-agility is so important and why SandboxAQ invests efforts in talent and new technologies to cover this urgent need.
